Dams are important infrastructure. They serve many purposes such as water supply, recreation, irrigation, and hydropower. However, if a dam fails, it can pose a serious risk to life and property downstream. Humans cannot do anything to prevent a dam-break with complete certainty. We can, however, plan for a potential dam-break. Dam breach modeling is part of this process. While models cannot perfectly depict reality, they can give us an idea of what areas would flood in the event of a dam break. As a result, this allows the dam owner and community officials to form a plan to warn and/or evacuate people in the event of an emergency related to the dam.
About Dam Breach Analyses
Dam breach analyses are performed for the purpose of evaluating the potential hazards associated with a dam failure. The maps produced as a result of a dam break analysis are often used to prepare an emergency action plan (EAP).
Dam Breach Modeling Software
There are several software programs used to prepare dam breach analyses. Some agencies specify the modeling software they will accept for dam-break inundation modeling work.
There are a number of programs that can be used for generating the dam breach hydrograph including HEC-1, HEC-HMS, BOSS, DAMBRK, FLO-2D, and Mike 21.
Typically, the modeling software used to route the downstream flood wave is a one-dimensional (1D) or two-dimensional (2D) hydraulic modeling software such as HEC-RAS or FlO-2D. In general, as the inundation area becomes less channelized, such as in urban settings, 1D analyses become less accurate. Another advantage of using 2D hydraulic modeling software programs is that they output the model results in a gridded format that is easier to map. HEC-RAS will be discussed in this blog post because it is freely available and widely used by dam safety professionals around the world.
Components of a Dam Breach Model
Dam breach inundation analyses include the following elements: identification of the most plausible dam failures, estimation of dam breach parameters, development of a dam breach outflow hydrograph, and routing of the dam breach hydrograph in the downstream area. In the following sections, I will briefly discuss each component of a dam breach model.
Keep in mind that this blog post is an introduction to setting up a dam breach model in HEC-RAS. Dam breach modeling can be very complex. There are many factors to consider when developing a dam breach model. Some of these factors include regulations, the type of dam, the type of dam breach (e.g., sunny-day or storm-induced), available terrain data, and the downstream area. These are things you should consider when developing a dam breach model in “real life.”
Evaluating Failure Modes
Firstly, consider the failure mode you will be modeling. A sunny-day failure occurs on a day with normal weather. In other words, the failure is not the result of a big storm or hydrologic conditions. A sunny-day failure is typically used to model a piping failure that may result from a geologic, structural, or seismic failure.
In contrast, a hydrologic or storm-induced failure occurs as the result of extreme precipitation. Typically, dam safety professionals will consider the probable maximum flood (PMF) when modeling a storm-induced failure. If you live in the United States, check out NOAA’s Probable Maximum Precipitation (PMP) Documents.
Calculating Breach Parameters
Secondly, determine breach parameters, which describe the nature of a dam breach. Breach parameters describe the geometry and formation time of a dam breach. For example, these parameters include the average breach width, the breach side slope, the breach height, breach progression (e.g., linear or sinusoidal), and the breach formation time. Although breach parameters are specific to each dam, there are several common methods dam safety professionals use to estimate breach parameters.
Dam safety professionals estimate breach parameters differently for earthen dams and concrete dams.
For embankment dams, dam breach prediction models are based on empirical data derived from earth and rockfill dam failure case studies. These equations relate dam breach properties of the dam and reservoir such as height, dam type, volume impounded, and shape of the reservoir. There are several equations that you can use to estimate the various parameters. However, the most common ones are listed below:
- Froehlich (1995b);
- Froehlich (2008);
- Von Thun and Gillette (1990);
- MacDonald and Langridge-Monopolish (1984); and,
- United States Bureau of Reclamation (1988)
In contrast, dam safety professionals estimate breach parameters for concrete dams based on the dam’s construction rather than equations. There are several types of concrete dams. Some of these include gravity dams, arch dams, multi-arch dams, and buttress dams. A gravity dam can also be combined with an arch dam to create what is known as a gravity-arch dam. I extracted the table below from the FEMA P-946 document. It shows a range of appropriate breach parameters for various types of concrete dams.
| Concrete Gravity Dams | Concrete Arch Dams | |
|---|---|---|
| Average Breach Width | Multiple of monolith widths | Entire dam width |
| Breach Side Slope | Vertical | Vertical to valley wall slope |
| Breach Formation Time | 0.1 to 0.5 hours | Nearly Instantaneous ≤ 0.1 hour |
Dam Breach Outflow Hydrograph
HEC-RAS can be used to develop a dam breach outflow hydrograph by creating a model containing the dam, reservoir, and a small area downstream for the purpose of obtaining the ouflow hydrograph. First, create a geometry file that contains the dam, reservoir, and a small area downstream of the dam. Next, enter the dam breach parameters into the dam breach data dialog box (see image below). Finally, enter your unsteady flow data.
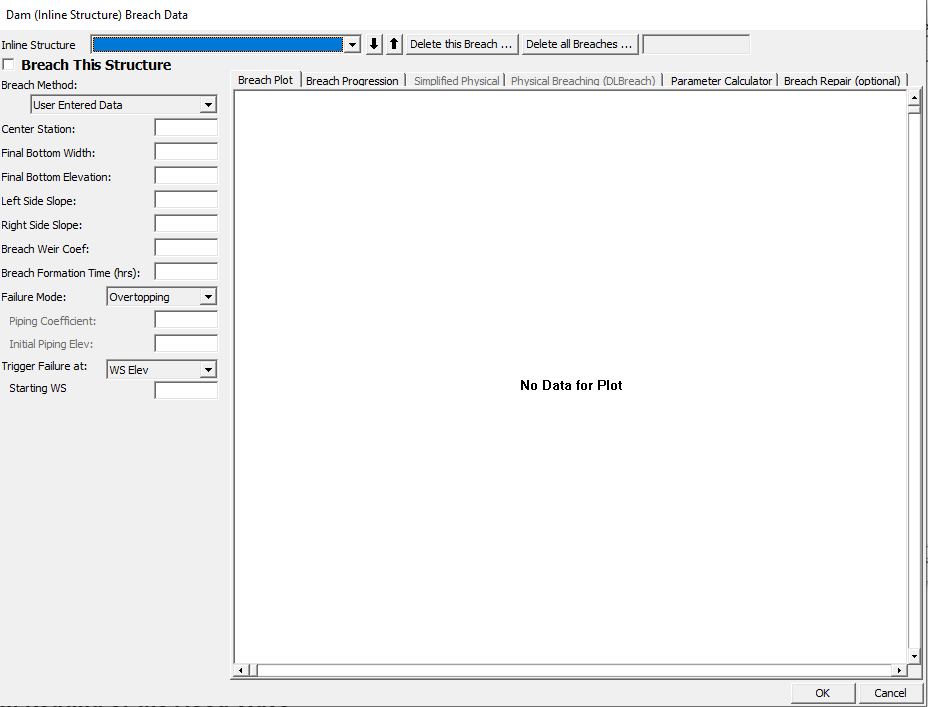
It is possible to combine the dam breach outflow step with the downstream routing step described in a subsequent section. However, this approach introduces instabilities that can be avoided by separating the dam breach outflow hydrograph step and the downstream routing step.
Representing Reservoirs in Dam Breach Modeling
The reservoir holds the water that is going to spill out of the “breach” to the downstream area. I typically represent the reservoir as a one-dimensional (1D) storage area element in HEC-RAS. This allows me to model the reservoir depletion using level pool routing. Although this is a more approximate way to model reservoir depletion, it is appropriate for most reservoirs. In addition, it is generally more stable. However, if you are modeling a longer reservoir, you may need to consider dynamic routing. This is a more physically-based way to represent reservoir depletion. In addition, dynamic routing requires constructing cross-sections of the reservoir.
Representing the Dam in Dam Breach Modeling
For two-dimensional (2D) HEC-RAS models, I represent that dam as a SA/2D Area Connection. This allows the user to enter the breach data they determined when estimating breach parameters.
Similarly, for 1D HEC-RAS models, I represent the dam as an inline structure.
Downstream Routing of the Flood Wave
Lastly, dam breach studies typically involve mapping the downstream extent of the water from a dam failure. This is accomplished by using hydraulic modeling software such HEC-RAS or FLO-2D to route the breach hydrograph through a downstream area.
For most of the dam break inundation modeling projects I have been involved in, we used HEC-RAS 2D to perform the downstream routing. Although it is possible to develop a 1D dam breach model, these types of models are difficult to stabilize and are often “messy.” It is worth noting that 2D models do take a very long time to run, especially if you are analyzing a large area with a fine mesh. Overall, it does seem like 2D modeling is becoming much more common in dam-break modeling (and hydraulic modeling in general). Therefore, I will focus on 2D models for the rest of this section.
When developing an HEC-RAS model, it is important to use the best terrain data you can find and to inspect your terrain data. Make sure that you add hydraulic structures where the terrain did not “pick them up.” However, you do not need to add every little culvert as many smaller pipes would be blocked by debris in the event of a dam break. Finally, add breaklines to orient cells along streams and channels.
Mapping
After performing the hydraulic modeling work, it is time to present the model results on maps that can be used for emergency planning in the event of a dam failure. Most consultants perform their mapping work in ArcGIS. Inundation maps typically contain the following elements:
- Map title and name of the dam,
- Description of the modeled dam failure scenario,
- Professional Engineer (PE) stamp,
- Map scale/scale bar,
- Depth grid that shows modeled flow depths greater than one foot,
- Velocity grid,
- Critical facilities (e.g., hospitals, schools, police stations),
- Arrival time (typically shown as contours or cross-sections),
- Flood severity (depth x velocity), and
- Distance downstream of the dam.
The required map elements depend on the agency reviewing the dam break inundation map and the dam’s hazard classification. The California Division of Safety of Dams (DSOD) has published examples of inundation maps on its website.
https://fmds.water.ca.gov/maps/damim/
Probabilistic Approach to Dam Breach Modeling
It seems like probabilistic hydraulic modeling is the way of the future for dam breach modeling, so I wanted to discuss it briefly. I have never performed a probabilistic hydraulic analysis for a project, but I have played around in McBreach.
Traditionally, dam breach parameters have been estimated through a deterministic approach, meaning that the modeler applies various equations to determine one (or maybe a couple) sets of parameters. The issue is that there is a lot of uncertainty around these dam breach parameters. Sensitivity analyses will show that peak outflow from a dam breach varies significantly depending on the breach parameters applied to the model. In contrast, a probabilistic approach to dam breach modeling involves analyzing random sets of breach parameters using a Monte Carlo Simulation. It would be quite time-consuming to manually input random sets of breach parameters into HEC-RAS. Fortunately, a group of engineers at the Kleinschmidt Group has developed a program to perform a Monte Carlo simulation for the purpose of determining appropriate breach parameters
Learn more McBreach by visiting the Kleinschmidt Group’s website:
https://www.kleinschmidtgroup.com/mcbreach/
The Australian Water School also published a webinar that discussed McBreach. It is available on YouTube.

Excellent write-up